在部分情况下,分支机构使用拨号上网,而且获取的还是私网地址(在运营商还会执行一次NAT)。只要总部有公网IP,分支机构还是可以使用IPsec连接到总部的,但只能由分支路由器发起IPsec连接。
在这种情况下,分支机构没有公网IP,而且还要经过运营商的NAT设备。在配置IPsec时,分支机构路由器的身份验证要使用名称的方式,因为经过NAT设备,IP会改变,所以无法使用IP作为IPsec设备的身份标识。如果使用名称作为身份标识,则IKE阶段1的模式就要使用野蛮模式(Aggressive mode)。
分支机构在NAT设备后面时,总部路由器的ipsec policy要使用模板(ipsec policy-template)。因为正常情况下,ipsec policy要指定对端设备的IP,但分支机构在NAT设备后面,总部路由器无法指定分支机构路由器的IP。如果使用模板,则不用指定对端设备的IP。
拓扑
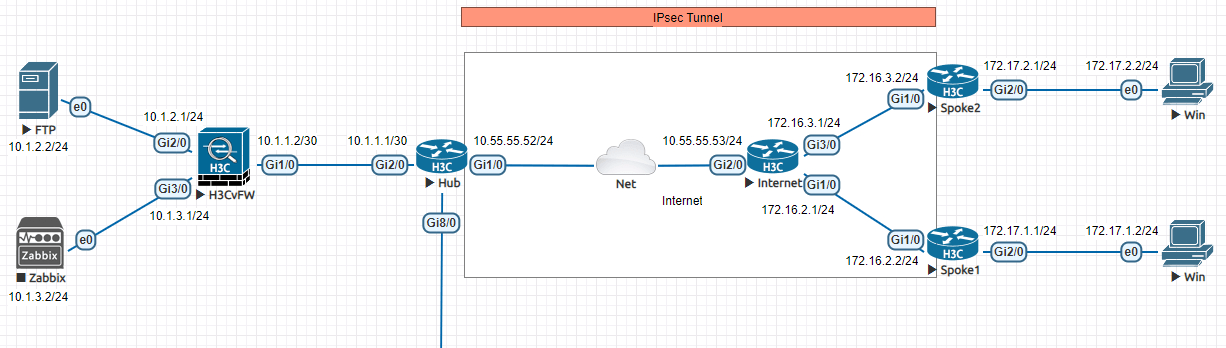
这个拓扑中包含两个IPsec VPN,一个是Hub和Spoke1,一个是Hub和Spoke2。Hub路由器有公网IP,Spoke1路由器有公网IP,Spoke2路由器没有公网IP。Hub和Spoke1之间的IPsec使用主模式,Hub和Spoke2之间的IPsec使用野蛮模式。
在Internet路由器配置NAT,对Spoke2的IP做地址转换, 以此模拟NAT环境。
配置
Hub路由器
[Hub]dis cu
#
version 7.1.064, Release 0621P18
#
interface GigabitEthernet1/0
ip address 10.55.55.52 255.255.255.0
nat outbound 3000
ipsec apply policy policy-1
#
interface GigabitEthernet2/0
ip address 10.1.1.1 255.255.255.252
#
ip route-static 0.0.0.0 0 10.55.55.1
ip route-static 172.16.2.0 24 10.55.55.53
#
acl advanced 3000
rule 10 deny ip source 10.1.2.0 0.0.0.255 destination 172.17.1.0 0.0.0.255
rule 15 deny ip source 10.1.3.0 0.0.0.255 destination 172.17.1.0 0.0.0.255
rule 20 deny ip source 10.1.2.0 0.0.0.255 destination 172.17.2.0 0.0.0.255
rule 25 deny ip source 10.1.3.0 0.0.0.255 destination 172.17.2.0 0.0.0.255
rule 1000 permit ip
#
acl advanced 3001
rule 0 permit ip source 10.1.2.0 0.0.0.255 destination 172.17.1.0 0.0.0.255
rule 5 permit ip source 10.1.3.0 0.0.0.255 destination 172.17.1.0 0.0.0.255
#
acl advanced 3002
rule 0 permit ip source 10.1.2.0 0.0.0.255 destination 172.17.2.0 0.0.0.255
rule 5 permit ip source 10.1.3.0 0.0.0.255 destination 172.17.2.0 0.0.0.255
#
ipsec transform-set trans-set-1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy-template template-1 10
transform-set trans-set-1
local-address 10.55.55.52
ike-profile profile-spoke2
#
ipsec policy policy-1 10 isakmp template template-1
#
ipsec policy policy-1 30 isakmp
transform-set trans-set-1
security acl 3001
local-address 10.55.55.52
remote-address 172.16.2.2
ike-profile profile-1
#
ike profile profile-1
keychain keychain-1
local-identity address 10.55.55.52
match remote identity address 172.16.2.2 255.255.255.255
proposal 1
#
ike profile profile-spoke2
keychain keychain-spoke2
exchange-mode aggressive
local-identity address 10.55.55.52
match remote identity fqdn spoke2
proposal 1
#
ike proposal 1
encryption-algorithm 3des-cbc
authentication-algorithm md5
#
ike keychain keychain-1
pre-shared-key address 172.16.2.2 255.255.255.255 key cipher $c$3$03X10VFR0Sq1BpPgANZ8P2zOuQZuMA==
#
ike keychain keychain-spoke2
pre-shared-key hostname spoke2 key cipher $c$3$9OLU5K2zCJ1Y6/zW1JhHNnbLtVCFiQ==
#
returnSpoke1路由器
[Hub]dis cu
#
version 7.1.064, Release 0621P18
#
interface GigabitEthernet1/0
ip address 172.16.2.2 255.255.255.0
mirroring-group 1 mirroring-port both
nat outbound 3000
ipsec apply policy policy-1
#
interface GigabitEthernet2/0
ip address 172.17.1.1 255.255.255.0
#
ip route-static 0.0.0.0 0 172.16.2.1
#
acl advanced 3000
rule 10 deny ip source 172.17.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
rule 15 deny ip source 172.16.1.0 0.0.0.255 destination 10.1.3.0 0.0.0.255
rule 1000 permit ip
#
acl advanced 3001
rule 0 permit ip source 172.17.1.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
rule 5 permit ip source 172.17.1.0 0.0.0.255 destination 10.1.3.0 0.0.0.255
#
ipsec transform-set trans-set-1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy-template template-1 10
transform-set trans-set-1
security acl 3001
local-address 10.55.55.53
remote-address 10.55.55.52
ike-profile profile-1
sa idle-time 86400
#
ipsec policy policy-1 30 isakmp
transform-set trans-set-1
security acl 3001
local-address 172.16.2.2
remote-address 10.55.55.52
ike-profile profile-1
#
ike profile profile-1
keychain keychain-1
local-identity address 172.16.2.2
match remote identity address 10.55.55.52 255.255.255.255
proposal 1
#
ike proposal 1
encryption-algorithm 3des-cbc
authentication-algorithm md5
#
ike keychain keychain-1
pre-shared-key address 10.55.55.52 255.255.255.255 key cipher $c$3$3g5t82J4iYiWSDvwzUOq3C8E6OVoYg==
#
returnSpoke2路由器
[Hub]dis cu
#
version 7.1.064, Release 0621P18
#
interface GigabitEthernet1/0
ip address 172.16.3.2 255.255.255.0
mirroring-group 1 mirroring-port both
nat outbound 3000
ipsec apply policy policy-1
#
interface GigabitEthernet2/0
ip address 172.17.2.1 255.255.255.0
#
ip route-static 0.0.0.0 0 172.16.3.1
#
acl advanced 3000
rule 10 deny ip source 172.17.2.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
rule 15 deny ip source 172.17.2.0 0.0.0.255 destination 10.1.3.0 0.0.0.255
rule 1000 permit ip
#
acl advanced 3001
rule 0 permit ip source 172.17.2.0 0.0.0.255 destination 10.1.2.0 0.0.0.255
rule 5 permit ip source 172.17.2.0 0.0.0.255 destination 10.1.3.0 0.0.0.255
#
ipsec transform-set trans-set-1
esp encryption-algorithm 3des-cbc
esp authentication-algorithm md5
#
ipsec policy policy-1 10 isakmp
transform-set trans-set-1
security acl 3001
remote-address 10.55.55.52
ike-profile profile-1
#
ike profile profile-1
keychain keychain-1
exchange-mode aggressive
local-identity fqdn spoke2
match remote identity address 10.55.55.52 255.255.255.255
proposal 1
#
ike proposal 1
encryption-algorithm 3des-cbc
authentication-algorithm md5
#
ike keychain keychain-1
pre-shared-key address 10.55.55.52 255.255.255.255 key cipher $c$3$lEp0jV5MgvQxXH0Y87mNxuMiDf12Lw==
#
return
```测试
查看连接后的信息
Hub路由器
[Hub]dis ike sa
Connection-ID Local Remote Flag DOI
-------------------------------------------------------------------------
229 10.55.55.52 172.16.2.2 RD IPsec
238 10.55.55.52 10.55.55.53 RD IPsec
[Hub]dis ipsec sa brief
-----------------------------------------------------------------------------
Interface/Global Dst Address SPI Protocol Status
-----------------------------------------------------------------------------
GE1/0 10.55.55.53 1296829538 ESP Active
GE1/0 10.55.55.52 4035185804 ESP Active
GE1/0 10.55.55.53 31648174 ESP Active
GE1/0 10.55.55.52 2094144089 ESP Active
GE1/0 10.55.55.53 247606592 ESP Active
GE1/0 10.55.55.52 2838397726 ESP Active
GE1/0 172.16.2.2 723266982 ESP Active
GE1/0 10.55.55.52 1233217591 ESP Active
[Hub]dis ipsec policy
-------------------------------------------
IPsec Policy: policy-1
Interface: GigabitEthernet1/0
-------------------------------------------
-----------------------------
Sequence number: 10
Mode: Template
-----------------------------
Policy template name: template-1
-----------------------------
Sequence number: 30
Mode: ISAKMP
-----------------------------
Traffic Flow Confidentiality: Disabled
Security data flow: 3001
Selector mode: standard
Local address: 10.55.55.52
Remote address: 172.16.2.2
Remote address switchback mode: Disabled
Transform set: trans-set-1
IKE profile: profile-1
IKEv2 profile:
smart-link policy:
SA trigger mode: Traffic-based
SA duration(time based): 3600 seconds
SA duration(traffic based): 1843200 kilobytes
SA soft-duration buffer(time based): --
SA soft-duration buffer(traffic based): --
SA idle time: --
SA df-bit:
[Hub]dis ipsec policy-template
-------------------------------------------
IPsec Policy Template: template-1
-------------------------------------------
-----------------------------
Sequence number: 10
-----------------------------
Traffic Flow Confidentiality: Disabled
Security data flow : 3002
Selector mode: standard
Local address: 10.55.55.52
IKE profile: profile-spoke2
IKEv2 profile:
Remote address:
Transform set: trans-set-1
IPsec SA local duration(time based): 3600 seconds
IPsec SA local duration(traffic based): 1843200 kilobytes
SA idle time: --
SA df-bit:
[Hub]dis ipsec global-info
IPsec anti-reply check: enable
IPsec anti-replay window (packets): 64
IPsec decrypt-check: enable
IPsec flow-redirect: disable
IPsec fragmentation: before-encryption
IPsec global-df-bit: copy
IPsec limit max-tunnel: --
IPsec redundancy: disable
IPsec sa global-duration time-based (seconds): 3600
IPsec sa global-duration traffic-based (KBytes): 1843200
IPsec sa idle-time (seconds): --Spoke1路由器
[spoke1]dis ike sa
Connection-ID Local Remote Flag DOI
-------------------------------------------------------------------------
6 172.16.2.2 10.55.55.52 RD IPsec
Flags:
RD--READY RL--REPLACED FD-FADING RK-REKEY
[spoke1]dis ipsec sa brief
-----------------------------------------------------------------------------
Interface/Global Dst Address SPI Protocol Status
-----------------------------------------------------------------------------
GE1/0 10.55.55.52 1233217591 ESP Active
GE1/0 172.16.2.2 723266982 ESP ActiveSpoke2路由器
[spoke2]dis ike sa
Connection-ID Local Remote Flag DOI
-------------------------------------------------------------------------
21 172.16.3.2 10.55.55.52 RD IPsec
Flags:
RD--READY RL--REPLACED FD-FADING RK-REKEY
[spoke2]dis ipsec sa brief
-----------------------------------------------------------------------------
Interface/Global Dst Address SPI Protocol Status
-----------------------------------------------------------------------------
GE1/0 10.55.55.52 4035185804 ESP Active
GE1/0 172.16.3.2 1296829538 ESP Active其他命令
reset ike sa
清除ike sa
reset要在用户模式下执行
reset ipsec sa
清除ipsec sa
reset ike sa connection-id 229
清除id为229的ike sa
reset ipsec sa remote 172.16.2.2
清除对端IP为172.16.2.2的ipsec sa
dis ike sa
dis ike sa verbose
dis ipsec sa
dis ipsec sa brief
dis ipsec policy
dis ipsec policy-template
dis ipsec global-info
dis ike statistics
dis ipsec statistics
dis ipsec tunnel
